- Home
- :
- All Communities
- :
- Products
- :
- ArcGIS Enterprise
- :
- ArcGIS Enterprise Questions
- :
- Re: Portal for ArcGIS 11.2 SAML login: logout from...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Portal for ArcGIS 11.2 SAML login: logout from IdP broken for oauth application
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Many users in my organization are complaining about a security issue because of Portal for ArcGIS SAML logout behavior: it does not propagate logout to identity provider and as a consequence, users remains logged in which is a security vulnerability.
I noticed the following: "Propagate logout to Identity provider" only works if logged in directly on Portal for ArcGIS (ie: OAuth client id ="arcgisonline"). If you are logged in on Portal for ArcGIS through an OAuth application (ie: OAuth client id ="o8WEYheNpQcE2dwwh"), then when signing out from another application, Portal for ArcGIS does not propage the logout and instead displays the following window:
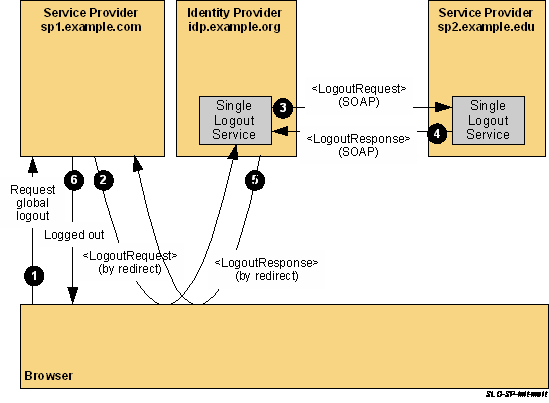
Let's illustrate this workflow with the diagram below:
Let's say "sp2.example.edu" is Portal for ArcGIS.
1. Working scenario when logged in directly on Portal for ArcGIS:
User is logged in on both Portal for ArcGIS and sp1.example.com and the user request a global logout from sp1.example.com. At step 3, Idp make a POST to sharing/rest/oauth2/saml/signout and the reply is the following:
<!DOCTYPE html>
<html>
<head>
<title>Posting request..</title>
<link href="/geoportal/sharing/rest/files/gw.css" rel="stylesheet" type="text/css"/>
<script language="javascript">
window.onload = function(e) {
document.forms[0].submit();
};
</script>
</head>
<body>
<form name="f" action="https://idp.example.org/auth/realms/company/protocol/saml" method="post">
<input type="hidden" name="SAMLRequest" value="foo" />
<input type="hidden" name="RelayState" value="bar" />
</form>
</body>
</html>
Note the form that will POST to Idp with "SAMLRequest" and "RelayState" parameters in order to sign out from Idp. It corresponds to step 4 and it works.
Now, let's compare it with the broken scenario:
2. Broken scenario when logged in indirectly on Portal for ArcGIS through an OAuth application:
User is logged in on Portal for ArcGIS indirectly through an OAuth application and on sp1.example.com and the user request a global logout from sp1.example.com. At step 3, Idp make a POST to sharing/rest/oauth2/saml/signout but this time the reply is the following:
<html>
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<meta name="referrer" content="origin">
<title>Sign In</title>
<script src="/geoportal/sharing/files/scripts/detector.min.js?__ARTIFACTID__"></script>
<link rel="stylesheet" href="/geoportal/sharing/files/css/site.min.css?__ARTIFACTID__">
<script src="/geoportal/sharing/files/scripts/theme.min.js?__ARTIFACTID__"></script>
<script>
var oAuthInfo = {"contextPath":"/geoportal/sharing","originSignin":false}
window.setTheme(oAuthInfo, "/geoportal/sharing");
</script>
<script src="/geoportal/sharing/files/scripts/oauth2.js?__ARTIFACTID__"></script>
</head>
<body>
<div class="content"></div>
</body>
<script>
oAuthInfo.locale = ((oAuthInfo.locale && oAuthInfo.locale === "iw") ? "he" : oAuthInfo.locale);
require.config({
baseUrl: "/geoportal/sharing/files/scripts/",
locale: oAuthInfo.locale && oAuthInfo.locale.toLowerCase() || ""
});
require(["signout-new", "domReady!"], function (signUp) {
signUp.startup(oAuthInfo);
});
</script>
</html>
which ends up to the page "You have been successfully signed out".
So coming back to our diagram, there is no longer a POST back to IDP and the logout process from IdP is broken in the middle because of Portal for ArcGIS. As a consequence, users are still logged in and as mentionned in the documentation:
If the user's web browser cache is not cleared, attempting to immediately sign back in to Portal for ArcGIS using the enterprise login option will result in an immediate login without needing to provide user credentials to the SAML identity provider. This is a security vulnerability that can be exploited when using a computer that is easily accessible to unauthorized users or to the general public.
Note that if you disable the "Propagate logout to Indentity Provider" option, you will have the same phenomena as in "Broken scenario when logged in indirectly on Portal for ArcGIS through an OAuth application" when logged in directly to Portal for ArcGIS.
As a conclusion, to me, the option "Propagate logout to Indentity Provider" should apply for all oauth client application ("argisonline" and all the others) and not solely to Portal for ArcGIS client.
Anybody else observing the same phenomena ? Any comments ? Did I miss anything obvious ?
Thanks,
Nicolas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Logged as:
BUG-000166664:
There is a security issue because of Portal for ArcGIS SAML logout behavior: it does not propagate logout to identity provider and as a consequence, users remains logged in which is a security vulnerability
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually, this BUG is a duplicate. This security vulnerability is known and logged since 2022 and still being analysed as:
BUG-000150121: When Portal for ArcGIS participates in an SLO SAML flow, it fails to redirect to the identity provider (IDP) following the session invalidation
 source:
source: